XStream
Introduction
XStream can convert JAVA objects and XML documents to each other.
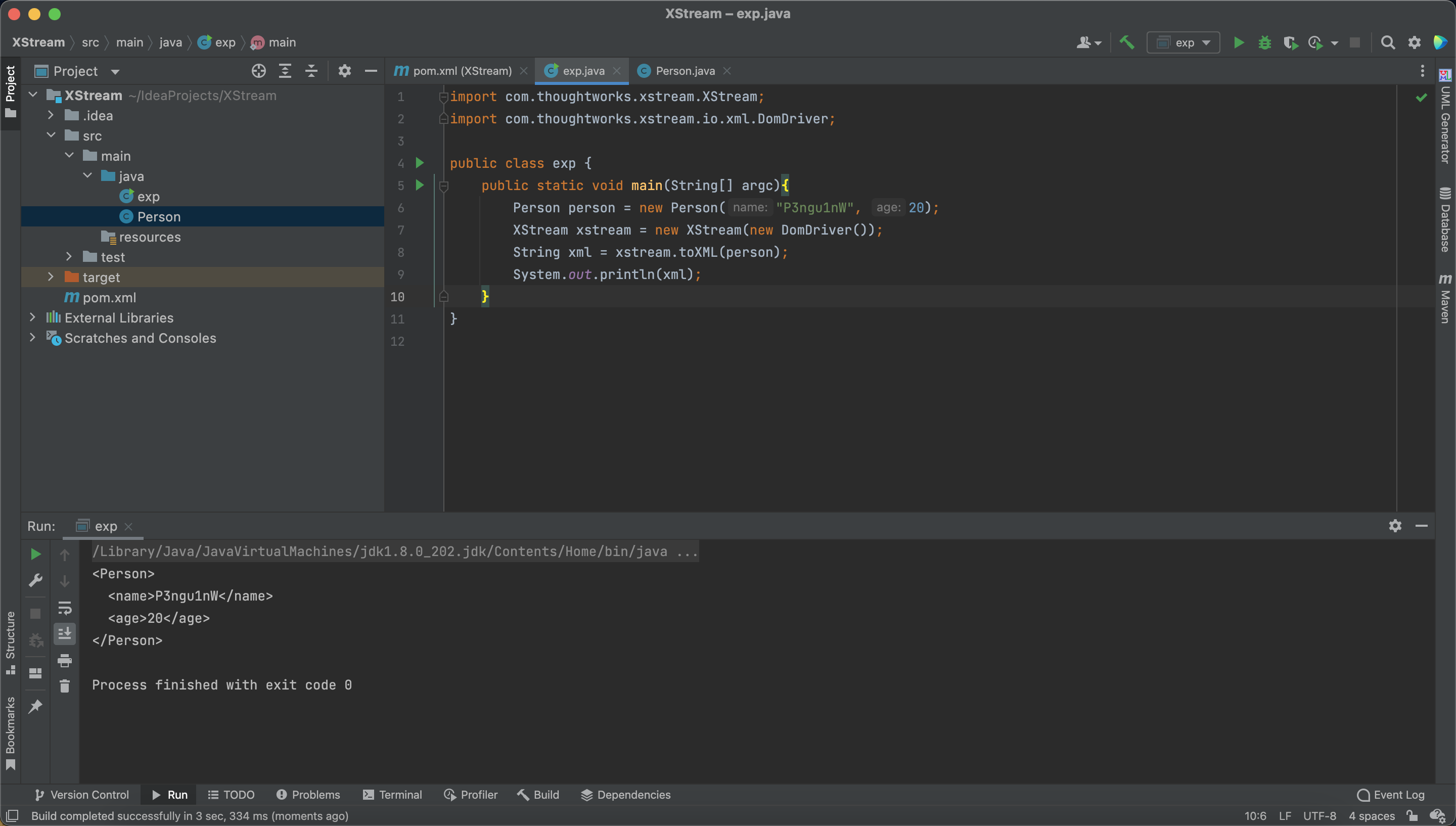
Let’s make a convert from JavaBean to XML.
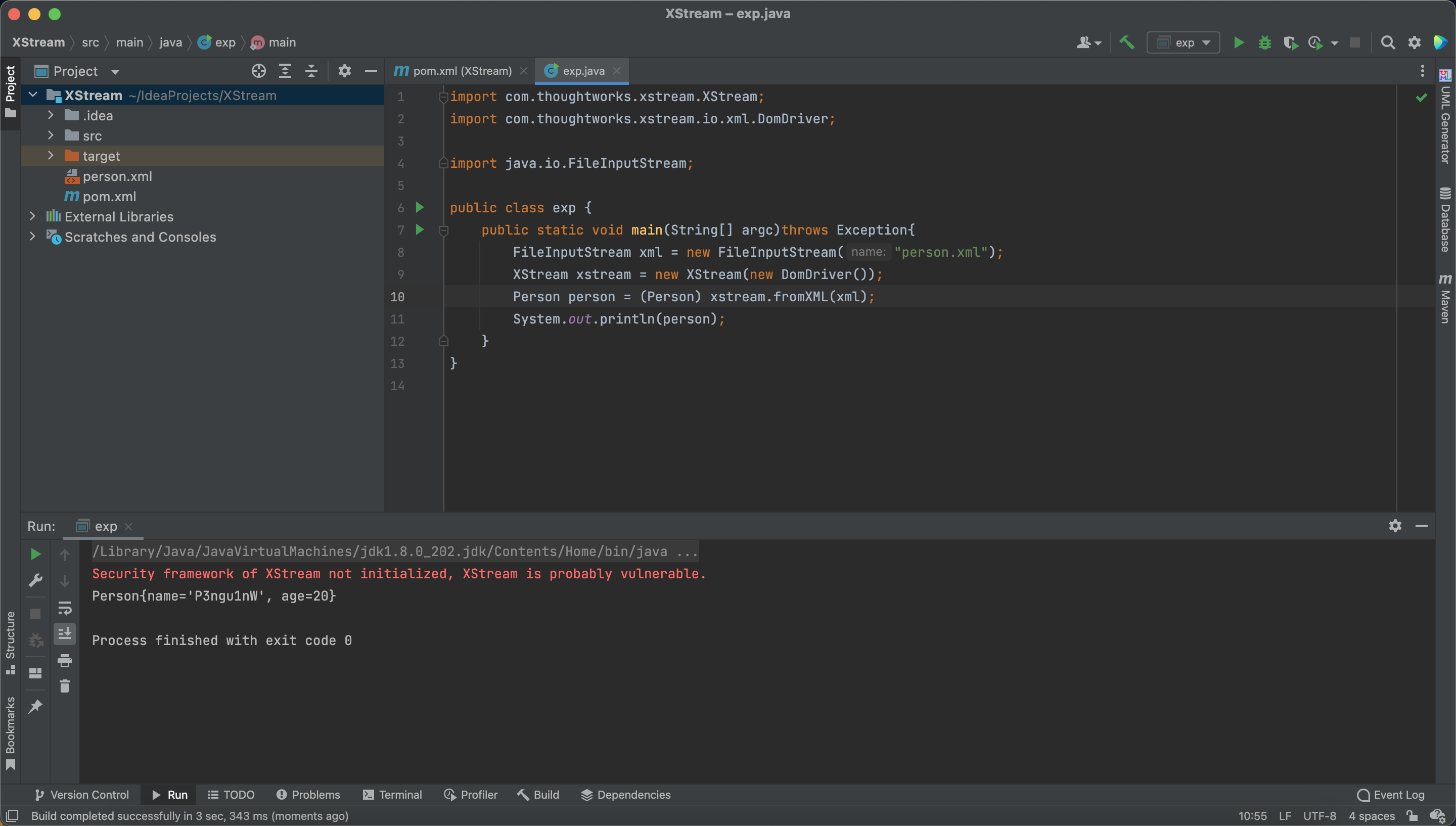
Also, we can convert from XML to JavaBean
CVE-2013-7285
env
1 | 1.3.1<XStream<1.4 |
EXP
1 | <sorted-set> |
Analyse
XStream supports a converter named DynamicProxyConverter, which can convert the content of the dynamic-proxy tag in XML into a dynamic proxy class object, and when the program calls the method declared by the interface class pointed to by the interface tag in the dynamic-proxy tag , the class method specified by the handler tag in the dynamic-proxy tag will be accessed through the dynamic proxy mechanism.
Using this mechanism, attackers can construct malicious XML content, that is, the handler tag in the dynamic-proxy tag points to a malicious class such as the EventHandler class that can implement reflection calls of any function, and the interface tag points to the interface class method that the target program will inevitably call. Finally, when the attacker inputs the malicious XML content from the outside, the deserialization vulnerability can be triggered to achieve the purpose of arbitrary code execution.
Blog to Learn
https://y4tacker.github.io/2022/02/10/year/2022/2/XStream反序列化/